Seamless worldwide performance with Geo
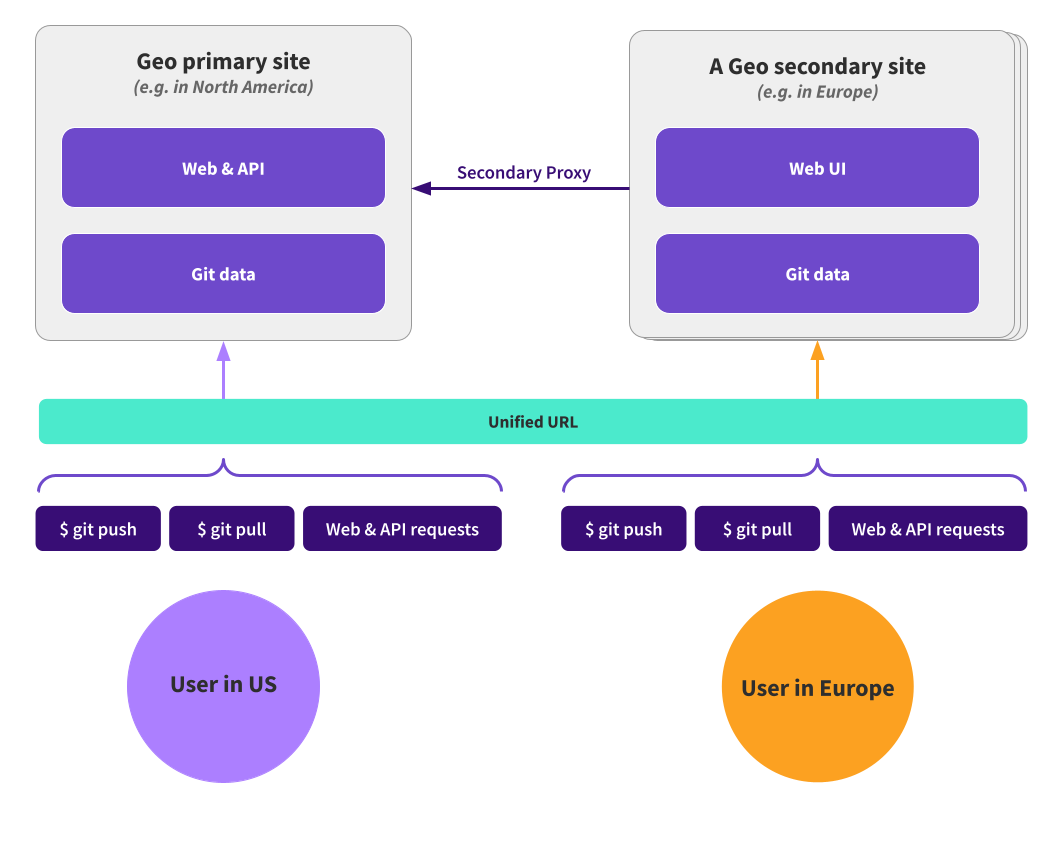
Organizations with geographically distributed teams use Geo to provide a fast and efficient experience across the globe. Before JiHu GitLab 14.6, you could set up Geo with a single, unified URL for all Git operations. However, Geo replicas each had their own URL for web UI and API access, so users had to know the URL to the specific Geo replicas they wanted to use. The web UI of the Geo replicas was also read-only, limiting users to viewing pages and requiring them to perform changes on the primary site.
In JiHu GitLab 14.6, Geo secondary sites transparently proxy write requests to the primary site while accelerating most read requests. Systems administrators can provide all JiHu GitLab users across their organization with a single URL that automatically uses the Geo site closest to them. Users no longer need to use different configuration to benefit from Geo, or worry about what operations won’t work on Geo secondary sites. Globally distributed teams now benefit from accelerated git clone or git pull commands, and a seamless worldwide experience.
Secondary proxying and unified URL support is enabled by default for new Geo installations. You can also set up a unified URL on an existing Geo installation and enable secondary proxying.
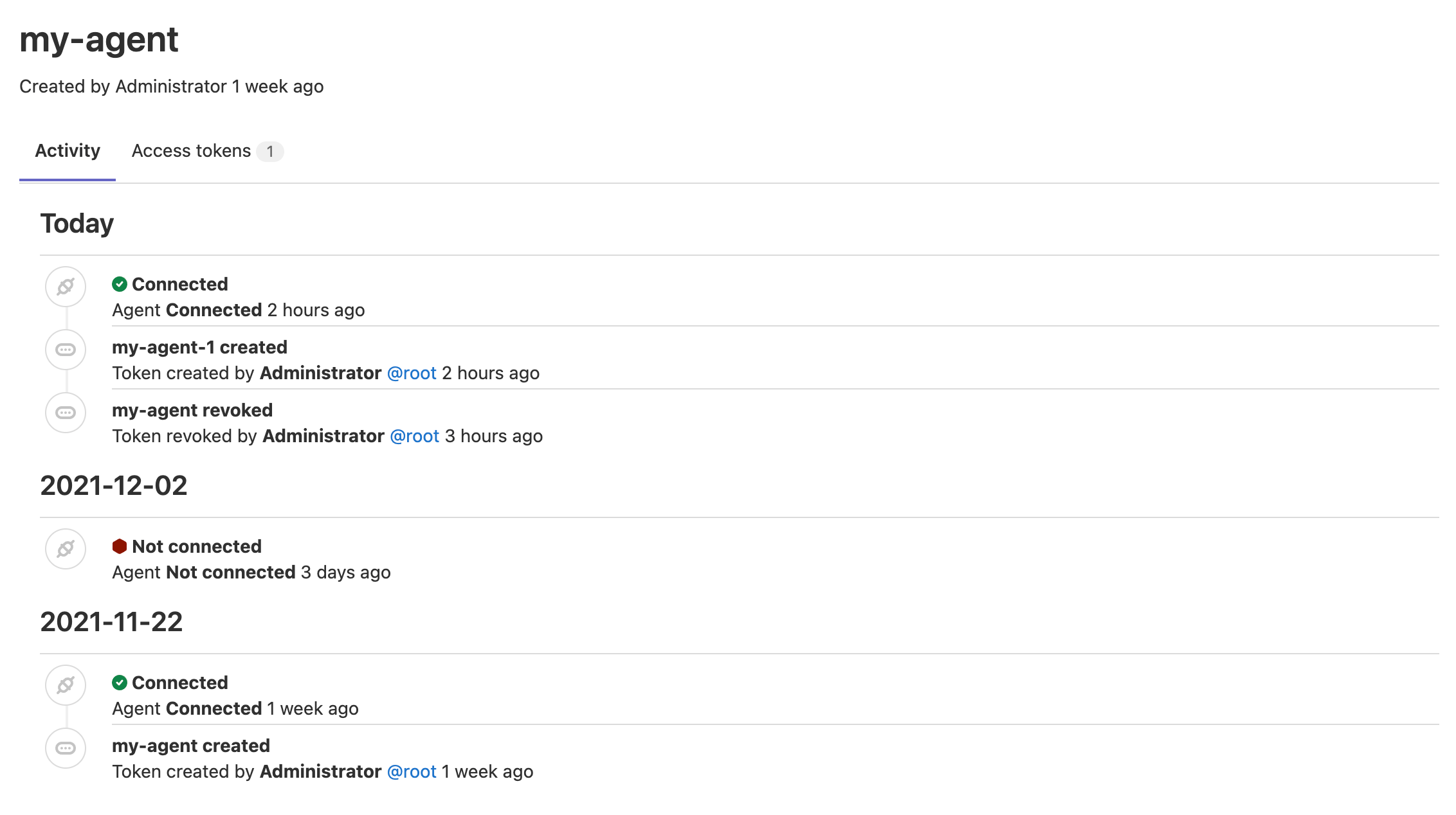
JiHu GitLab Agent’s activity information
Being able to monitor your cluster’s activity helps you detect and troubleshoot faulty events, and rest assured when they succeed.
JiHu GitLab now ships with an activity list for the JiHu GitLab Agent that logs real-time events. This first implementation logs connection and token statuses and will be followed with more events in future releases. We also plan to provide a similar solution to track CI/CD Tunnel events, for which your early feedback is more than welcome.
Toggle wiki editors seamlessly
Editing wiki pages with the new rich Markdown editor makes it easier for everyone to contribute regardless of how well they know Markdown syntax. You may also prefer to write raw Markdown in some situations, but use the WYSIWYG interface for more complex or tedious formatting tasks, like creating tables.
Previous versions of JiHu GitLab required you to save changes before switching between the rich Markdown editor and the Markdown source, adding more steps and friction to your edits. In JiHu GitLab 14.6 you can now seamlessly switch between the two editing experiences without committing your changes, choosing the editor that suits your needs at any given moment.
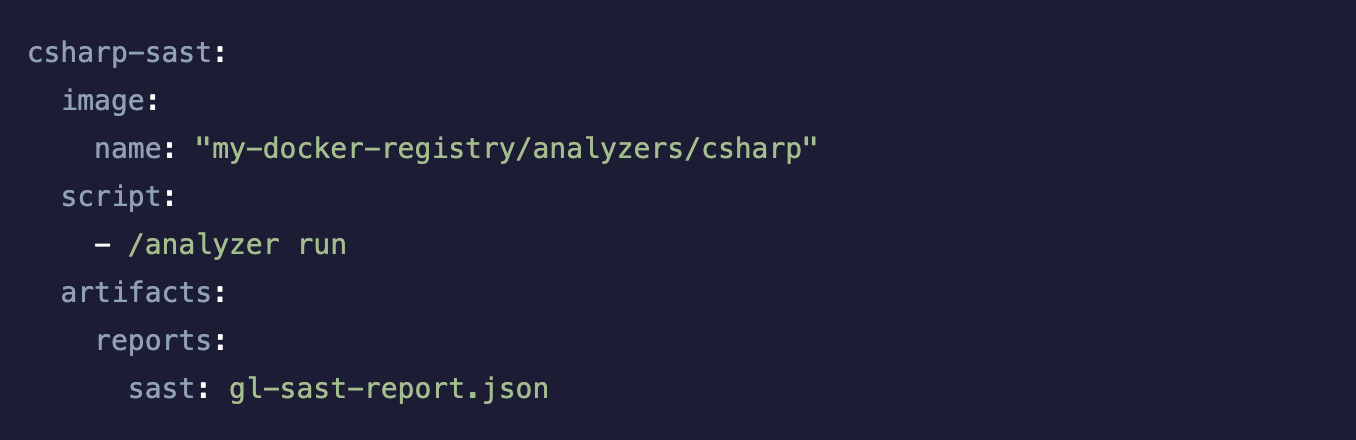
SAST Support for .NET 6
Microsoft’s release of .NET 6.0 is the next major release of .NET Core, which contains both massive performance gains and new compute options, and should enable simplified .NET code. We have updated our .NET SAST analyzer, Security Code Scan, to support this new version, which is also now supported with our SAST language detection, allowing JiHu GitLab SAST to automatically detect .NET 6 projects. This change was part of a community contribution by @vasyl11 at Clay Solutions, who we thank for their efforts.
Due to backwards compatibility concerns, if you want to leverage this new .NET 6 SAST scanning, you will need to update your .gitlab-ci.yml file to pin to the new major version of Security Code Scan. You can add this code snippet to your .gitlab-ci.yml file to try these new scanning capabilities. In a future release, we will announce the upcoming deprecation and removal in JiHu GitLab 15.0 of any version of .NET before 3.0 for SAST scanning, due to its end of Life and last support date status with Microsoft. In JiHu GitLab 15.0, we will promote this new version of Security Code Scan to run by default, which will enable .NET 5 and 6 SAST scanning without the need for the experimental flag.
SAST scan execution policies
Users can now require SAST scans to run on a regular schedule or as part of project CI pipelines, independent of the .gitlab-ci.yml file’s contents. This allows security teams to separately manage these scan requirements without allowing developers to change the configuration. You can get started with security policies on the Security & Compliance > Policies page. To specify SAST scans, set the scan field to sast.